[ad_1]
Logon is an occasion in Home windows that exhibits {that a} consumer account is being granted some entry to a workstation/server/laptop. This text will clarify the fundamentals of Home windows logon varieties, how authentication performs a job, after which describes the several types of logon constructed into Home windows.
As IT professionals, all of us have ‘logged in’ computer systems, servers, community units, and so on. However, what precisely does logging in Home windows imply? Are there a number of login varieties supported in Home windows? There definitely are, most likely greater than you notice.
Understanding Home windows logon varieties
As I discussed earlier, there are a plethora of login varieties in Home windows. Nonetheless, logging on to Home windows and being authenticated are separate actions/occasions.
logon vs authentication
A Home windows logon happens on the workstation a consumer is making an attempt to entry. Nonetheless, Home windows authentication is carried out by the pc the place the consumer account is saved. Sure, it is a delicate distinction, particularly while you get into native, interactive and community logon and authentication.
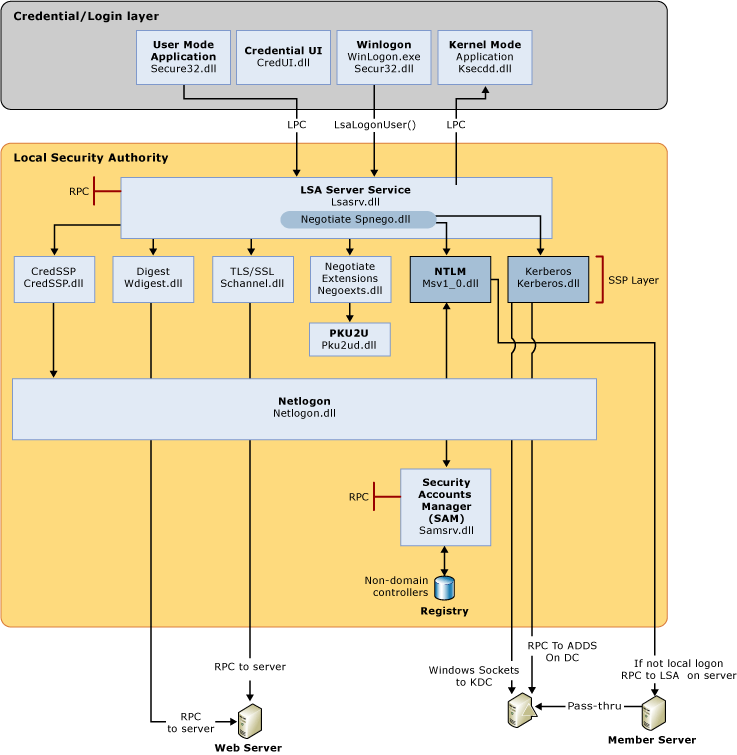
In Home windows-based computer systems, all authentication is processed as one of many logon varieties under. That is true no matter which authentication protocol or authenticator is used.
Interactive logon with native or area accounts
One interactive logon A logon is whereby the consumer makes use of the native keyboard and mouse to enter credentials into the logon display in Home windows. They a. can go browsing with native account In opposition to a neighborhood SAM (Safety Accounts Supervisor) account database, utilizing the pc identify within the ‘Area’ discipline.
Customers can go browsing to a area account By deciding on Lively Listing domains within the Area discipline or by typing of their UPN within the Username discipline. Good playing cards and biometric units may also be used as authentication strategies to log in interactively.
distant interactive logon
Once you provoke a Distant Desktop Protocol (RDP) session on one other workstation or server, it’s a distant interactive login. You are logging in from the distant machine interactively, however you are doing it remotely. It’s not the pc you might be utilizing to provoke that connection.
The distinction is comparatively easy on paper, however there are numerous nuances to how they’re reported, logged in varied safety occasion logs, and the way they are often exploited or compromised with out your information.
community logon
A community logon happens when a consumer logs on to a machine on the community. That is often for accessing shared community sources. For instance, accessing a shared folder, WinRM (Home windows Distant Administration Protocol), or connecting to a machine by way of a printer.
Enabling Logon Occasions on Home windows
By default, area controllers will generate a logon occasion when a site laptop is logged on. Nonetheless, there are extra strong occasions that may be logged: audit account logon occasion And audit logon occasion, You may accomplish this via a gaggle coverage in your area, or via their respective native safety coverage on a particular member server or workstation.
Listed below are some primary directions for enabling logging with Group Coverage in an Lively Listing area surroundings:
- Login to your area controller.
- Open the Group Coverage Administration Console in Administrative Instruments.
- increase your workspace Factor.
- increase the group coverage gadgets Factor.
- right-click on default area coverage object and click on edit,
- Observe the trail: Home windows Settings -> Safety Settings -> Superior Audit Coverage Configuration -> Audit Insurance policies -> Logon/Logoff -> Audit Logon.
- Choose ‘Configure the next audit occasions:’ success And Failure checkbox.
Now I’m going to element the commonest Home windows logon varieties. For every of them, I am going to embody the sorts of authenticators which can be able to initiating this sort of logon, in addition to sensible examples.
Logon Sort 2: Interactive Logon
The sort of logon is generated when a consumer logs on to the console of a machine. Once more, the consumer may use good playing cards or biometric strategies along with the normal keyboard and mouse.
Authenticator accepted
You should use keyboard and mouse, good playing cards and biometric units. New tools varieties have been launched in recent times, together with FIDO2-compatible security units (Yubikey, and so on.).
Instance
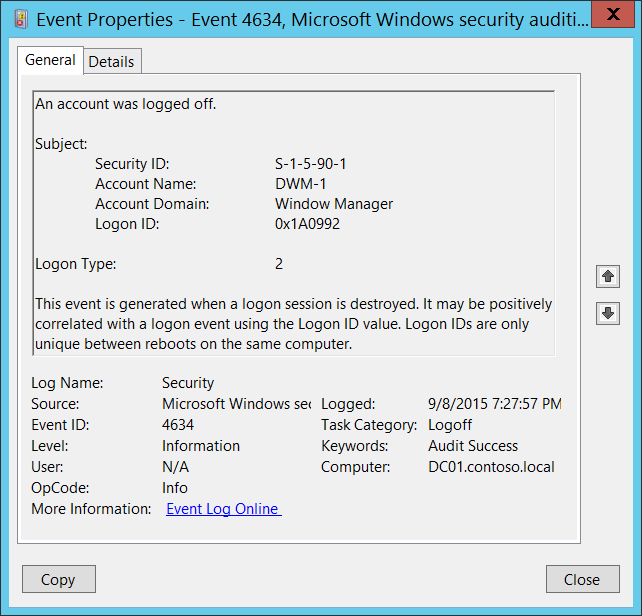
Native logon permits the consumer to entry sources on the native laptop. Native logon requires a consumer account within the native SAM on the pc.
Logon Sort 3: Community Logon
This logon sort describes a pc that’s being accessed throughout the community (LAN/WAN). It’s generally used to entry file servers, printers, and different community units.
Authenticator accepted
You should use a keyboard and mouse (password), a Kerberos ticket, and NT hash all accepted authenticators for this sort of logon.
Instance
A community logon permits a consumer to entry mentioned sources (by way of a token). Native authentication must be accomplished first.
Logon Sort 4: Batch Logon
This logon sort is mostly associated to scheduled duties, Logon Sort 4 occasions are often benign, nonetheless, a malicious consumer might attempt to guess an account’s password right here.
Authenticator accepted
A password is the one accepted authenticator as a result of it’s native.
Instance
When Home windows performs a scheduled job, the service creates a brand new logon session for the duty in order that it has the required permissions to finish it.
Should you return in time by a number of years, you may keep in mind the ‘at’ command. Sure, for nostalgia’s sake, learn this documentation hyperlink from Microsoft throughout the Home windows 2000 days!
Logon Sort 5: Service Logon
The following sort known as service logon. When Home windows begins a service that’s configured to go browsing as a consumer, Home windows creates a brand new logon session. Every service is configured to run as a specified consumer account.
Authenticator accepted
Like batch logon, the service logon sort solely accepts a password which is often saved as an LSA secret.
Instance
When establishing a neighborhood Apache Tomcat server to host a web site, you possibly can configure the Tomcat service to go browsing as an administrator (not a good suggestion), or ideally a site service account with a really robust password.
logon sort 7: unlocked
When a consumer leaves the workstation for a time frame, Home windows will lock the pc. That is to guard the workstation, its information, and different potential distant community information from attackers or native hackers. When a consumer unlocks the pc, this logon sort is logged within the native safety occasion log.
Authenticator accepted
Once more, just one password is accepted for this logon sort.
Instance
As acknowledged above, after returning to a pc locked by the coverage, unlocking the pc, by re-entering the password, describes this phenomenon.
logon sort 8: community clear textual content logon
This sort is much like a community logon (Sort 3), however right here the password was despatched in cleartext over the community. The password was handed to the authentication system on the distant system in an un-hashed type. Home windows at all times hashes the typed password earlier than transmitting it over the LAN.
Authenticator accepted
You guessed it… Password.
Instance
The one conventional instance of this was IIS (Web Info Providers) nameless logins, however they’ve additionally turn into uncommon as a result of ever-increasing safety panorama we reside in as we speak.
One other instance is inside an ASP (Software Service Supplier) script utilizing the ADVAPI logon course of.
Logon Sort 9: New Credential-Primarily based Logon
This logon sort describes utilizing RunAs to begin packages below a unique account than the logged-in account. You employ the /netonly swap in Home windows to perform this.
Authenticator accepted
For this logon sort solely password is accepted as authenticator.
Instance
while you wish to open laptop Administration As a unique area administrator, you possibly can maintain down Shift while you right-click Instruments in Administrative Instruments, then click on run as one other consumer, Right here, you are accessing this logon sort to open packages below a unique account than the one you utilize to log into the workstation.
Logon Sort 10: Distant Interactive Logon
This logon sort is typically known as “RemoteInteractive”, an outline for accessing distant workstations or servers utilizing the Distant Desktop Protocol (or Terminal Providers). That is much like sort #2 (interactive), however once more, we’re coming from a distant location.
Authenticator accepted
Since we’re utilizing RDP, we have now the identical authenticators attainable. We will use good playing cards and biometric units so long as they’re handed into the RDP consumer software program with the suitable settings.
Instance
The one prime instance is once more utilizing RDP to hook up with a distant laptop on the community.
Logon Sort 11: Cached Interactive Logon
Our final sort tells when a consumer logs on to the machine by way of cached credentials. That is very comparable, once more, to #2 (Interactive), however as a substitute of ‘reside’ authentication to a site controller, Home windows makes use of beforehand entered (cached) credentials to permit consumer entry to the workstation regionally. does.
Authenticator accepted
On this instance, solely passwords are attainable. There isn’t a means to make use of a cached good card token for apparent causes.
Instance
The commonest instance right here is when your laptop or workstation doesn’t have a community (LAN/WAN) connection. As a result of Home windows can not make real-time authentication requests to a site controller till ‘x’ variety of days have elapsed since your workstation talked to For a site controller, native cached credentials are used to offer native authentication.
Once more, Group Coverage can specify what number of days your laptop can stay within the ‘grace interval’. Normally, it’s 30 or 90 days. However, with a security minded, the much less the higher.
conclusion
Having a sound information of the totally different logon varieties in Home windows helps IT professionals perceive and troubleshoot points with varied logon occasions in Occasion Viewer. And from a safety standpoint, it’s possible you’ll be analyzing your area controller safety occasion logs whereas making an attempt to trace down malicious exercise in your Home windows area.
Thanks for studying. Please depart a remark under!
[ad_2]
Supply hyperlink